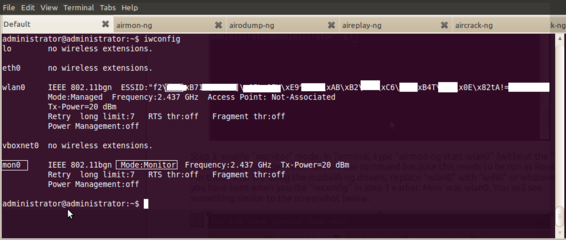
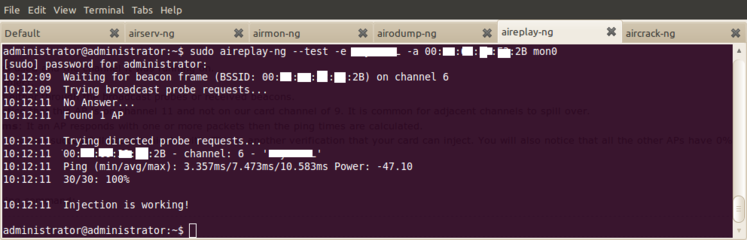
As of now, Aireplay-ng only supports injection on Prism2, PrismGT, Atheros, Broadcom (with the b43 driver), Intel IWL, RTL8180, RTL8187, Ralink, ACX1xx and Zydas. Injection on Hermes, Aironet and Marvell is not supported because of firmware and/or driver limitations.
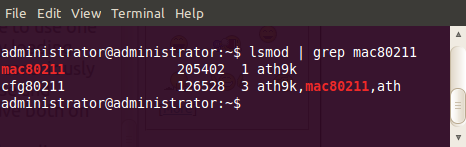
There are two families of drivers - ieee80211 and mac80211. Basically, mac80211 has largely replaced ieee80211.
See this write-up for more detail. Where the mac80211 version of the driver is stable and supports injection, that should be your first choice. Keeping in mind that mac80211 is only well supported starting in about 2.6.25 and up kernels. However, in some cases, only legacy ieee80211 drivers exist for injection.
Nearly all non-mac80211 drivers that can support injection need to be patched to support injection in Monitor mode. On the other hand, the mac80211 versions of the drivers generally only need the mac80211 core itself patched to support the fragmentation attack. Other attacks using mac80211 drivers typically work without patching.
Remember you cannot use both ieee80211 and mac80211 versions of the same driver at the same time. You must decide to use one or the other, not both. If you try loading both, one will fail. So you must consciously decide which one you wish to use and blacklist the other one if you have both on your system.








 ay mali
ay mali